Risks of not having Multi-Factor Authentication (MFA)

It's encouraging to see more users implement multi-factor authentication or MFA to create an extra layer of security to prevent cybercriminals to gain unauthorised access. Even the most basic security measures cannot prevent cyberattacks.
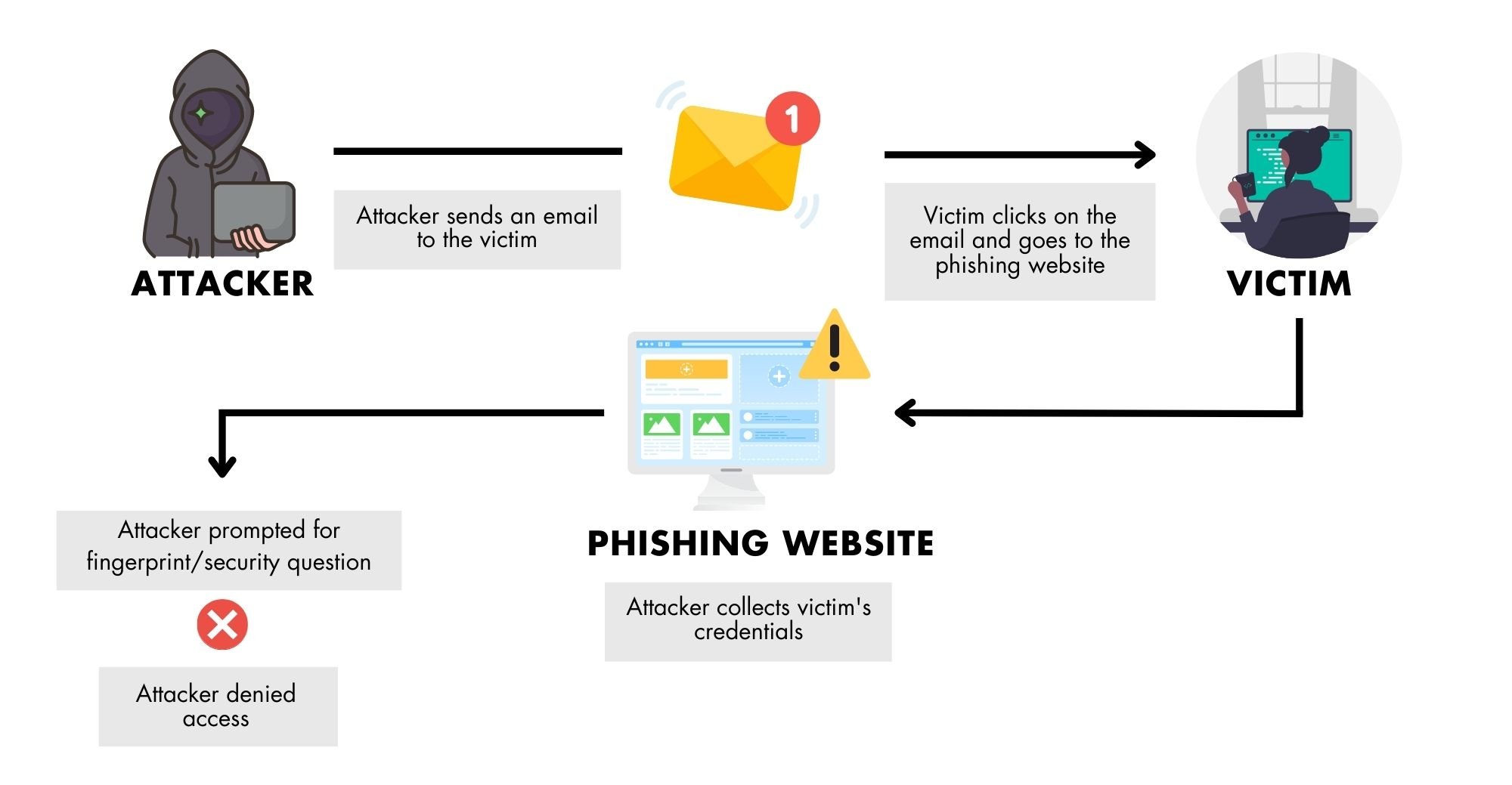
Phishing is an alarmingly simple method to obtain user information and to deceive users into disclosing their sensitive information such as login credentials. Cybercriminals will send their victims phony emails and make bogus phone calls. The following are the most typical indicators of a phishing email, according to Phishing.org:
- The email seems too good to be true
- The email has a sense of urgency
- Suspicious hyperlinks in the email
- Suspicious attachments in the email
- Unusual sender
Scammers can obtain user information in a variety of additional ways than phishing and use sophisticated tools to carry out brute force attacks, create random passwords and determine your login details. Keyloggers can be used to record each keystroke as well.
2020 saw a cost to cybercrime of over $1 trillion, ransomware attacks affecting 37% of enterprises, and malware attacks affecting 61%. These facts demonstrate that businesses must deal with a wide range of dangerous cybercrimes. They require strong cybersecurity controls and procedures like multi-factor authentication to safeguard their networks, systems, and data (MFA)
Types of cyberattack MFA Protects:
- Phishing
- Spear phishing
- Keyloggers
- Credential stuffing
- Brute force and reverse brute force attacks
- Man-in-the-middle (MITM) attacks
MFA for Stronger Security

Users of conventional single-factor authentication systems enter password as a verification factor to access a system, application or website. These passwords are simple to acquire by hackers, who then use them to access corporate systems.
To authenticate a user's identity and enable them access to an account, MFA systems demand two or more factors. MFA reduces the likelihood of illegal access by offering trustworthy confirmation that an authorized user is who they claim to be. For these reasons, MFA is substantially more successful than passwords at securing systems.
How do different types of attack work?
Let's first go over how these cyberattacks function in order to comprehend how MFA defends against them:
Phishing
In 2020, phishing attacks affected 75% of global enterprises. The most frequent attack in data breaches was phishing.
An email is a tool used in phishing attacks, whereby the cybercriminal poses as a prominent entity that the intended victim would typically trust, like a bank or a government agency. The attacker then creates a phoney email that appears to be from a reputable company but actually contains a malicious attachment or link.
The goal is to trick the victim into doing anything that will benefit the attacker. For instance, they might be instructed to use their login information to conduct certain transactions on the offered (false) URL. The attacker takes the user's login information and logs onto the legitimate website using the user's identity.
Spear Phishing
In spear phishing, the attacker sends well-crafted, believable, and relevant communications to specific individuals or organisations. To increase the credibility of the message, they usually include customised material, such as the user's name, or a reference to recent user activity (such as an online purchase or event like a wedding).
Spear phishing emails, like phishing emails, feature a forceful call to action aimed to compel recipients to give sensitive information, such as account login credentials or financial information.
Whaling
Whaling is a targeted spear phishing tactic that targets a senior or high-profile victim, such as a C-suite boss. Because these individuals are often more tech-savvy, "normal" phishing attempts frequently fail to mislead them. As a result, fraudsters use more advanced approaches and individualised, targeted phoney communications to the victim. Attackers may use urgency to persuade a victim to open an attachment containing malware or to begin a wire transfer.
Key Loggers
A keylogger is a type of spyware or surveillance application. Cybercriminals regularly utilise viruses to install keyloggers on a victim's device. The programme records every keystroke the victim makes such as usernames, passwords, replies to security questions, banking information, credit card information, websites visited, and more. Cybercriminals then utilise the sensitive data for illegal purposes.
Brute Force
A cybercriminal launches a brute-force attack by creating and testing a huge number of login and password combinations in the hopes that at least one of them would gain access to a business system. Brute-force attacks are quite common and provide hackers various benefits:
- Place spam ads on websites to make money when the ad is clicked or viewed
- Infect a site’s visitors with activity-tracking spyware, steal their data, and sell it to marketers (or on the dark web)
- Hack into user accounts to steal personal data, financial data, or money
- Spread malware or hijack enterprise systems to disrupt operations
A reverse brute-force attack involves the attacker attempting popular passwords, such as "password" or "123456," in an effort to brute-force a username and obtain access to numerous accounts.
Dictionary assaults are a frequent kind of brute force attack in which the attacker attempts every password in a dictionary to get access.
Passwords are also used in a brute-force attack known as credential stuffing. Many people use the same username and/or password on multiple accounts. This enables attackers to carry out attacks known as credential stuffing, in which they steal credentials and attempt to use them to gain access to numerous accounts. They occasionally acquire credentials from one company, either through a data breach or through the dark web, and use them to access user accounts at another company. They anticipate that at least some of the same credentials will allow them to access user accounts at both companies.
Brute-force attacks summary: (can turn into graphics)
- Sell access to compromised accounts
- Steal identities
- Perpetrate fraud
- Steal sensitive enterprise information, e.g. business secrets, Personally Identifiable Information (PII), financial information, intellectual property, etc.
- Spy on the enterprise (corporate espionage)
Man-In-The-Middle Attack
During a Man-in-the-attack or MITM attack, the attacker listens in on a user's connection with another party. They listen in on or intercept conversations between these parties with the intent of corrupting data, stealing user passwords or personal information, or destroying communications.
How MFA Combats Common Attacks?
All of these hacks include the collection of login information. MFA requires users to provide additional information or credentials in order to access an account. As a result, if an attacker is successful in collecting passwords, it is unlikely they will be able to steal or compromise the other authentication elements required for MFA. As a result, MFA can successfully dissuade hackers and combat a variety of threats, which will be discussed more below.
Phishing, Spear Phishing and Whaling
An attacker may employ phishing to gain a user's login information. The attacker will be unable to access the user's account if MFA is employed to safeguard it. This is because a phishing email will not include additional authentication factors such as one-time passwords (OTPs) supplied to a separate device (such as a mobile phone), fingerprints, or other biometric aspects required to access the system.
When employing some versions of MFA, such as WebAuth, in assaults where the attacker tries to trick the user into entering their credentials, the user must submit a YubiKey or fingerprint from the machine from which they are logging in. The system and user are safe since the attacker cannot get these details.
Keyloggers
Keyloggers can record any credentials entered into a system. Nevertheless, if MFA is enabled, simply obtaining the password is insufficient. In order to log in, they must also have access to the additional authentication factors. If MFA is configured with a mobile authenticator app, the authorised user merely needs to sign in with their mobile device and accept the auth request. Fraudsters cannot access the system without this additional device, even if a keylogger is installed on the user's machine.
Credentials Stuffing
Credential stuffing attacks, in which fraudsters test a list of stolen usernames and passwords on multiple websites at the same time, can be efficiently prevented by MFA. Yet, the cybercriminal would want additional information to authenticate and log in with MFA. They won't be able to gain unauthorised access to the company's networks because they won't have this knowledge.
Brute Force Attack
An attacker may be able to find a legitimate account and password via brute force, reverse brute force, or dictionary attacks. They are unable to access the system, however, since they do not understand or have access to the additional authentication requirements required by the MFA system.
How Does MFA Prevent Ransomware/Extortion ware?
Ransomware is another rising cybersecurity concern for businesses (extortion ware). In the United States, for example, cybersecurity threats increased by 139% between 2019 and 2020. In reality, 145.2 million cases were reported in just the third quarter of 2020. Nevertheless, ransom payments increased by 311%, reaching around $350 million in bitcoins.
Ransomware is malware that an attacker secretly installs on a user's computer. The software encrypts the data or files of the user. The attacker demands a ransom from the victim in order to decrypt these encrypted files and re-grant access to the user.
MFA is extremely effective in preventing ransomware attacks as well as traditional hacks. A ransomware attack begins when an attacker gets account credentials. But, with MFA, the attackers lack the additional information required to gain access to the target account. This prevents the attack and keeps it from entering the system.
Furthermore, when IT administrators start receiving unusual MFA authorization requests, any unlawful login attempts will trigger an alert. Then, they can act right away to keep these assailants out. Organizations can fend off ransomware attacks and shield themselves from pricey extortion demands by employing MFA.
Conclusion
MFA cannot guarantee foolproof security or stop all cyberattacks. However, it can help protect high-value systems and accounts, secure email access, and limit the usefulness of stolen credentials. Most importantly, MFA adds additional layers of authentication to protect systems and combat many types of cyberattacks. MFA is also critical to achieving Zero Trust, the most reliable cybersecurity approach in the modern cyber threat landscape.
