Office 365 TLS Deprecation
.png)
Recently, Microsoft announced an important update: "We are deprecation 3DES (Triple Data Encryption Standard) in Office 365".
3DES cipher is widely used in TLS / SSL encryption for HTTPS and SSH traffic. As of 2016, it has been marked as a threat due to the SWEET32 attacks (Attackers found small fragments of plain text when encrypted with 3DES) and planned a complete withdrawal of use before 2023. To provide data protection, Microsoft has made changes to the TLS service.
Before you get into the process of planning 3DES removal, let's see how TLS and how 3DES removal affects TLS.
What is TLS?
Transport Layer Security (TLS) is a confidential protocol that provides secure network communication. For example, Websites use TLS to protect all communications between their servers and browsers / clients. There are currently 4 versions of the TLS protocol in use today: TLS 1.0,1.1,1.2 and 1.3.
Why Office 365 moving to TLS 1.2?
Microsoft plans to move all of its online services to TLS 1.2 or later to provide better encryption for its customers. From 28 February 2019, Microsoft will begin withdrawing 3DES. As a result, if your current connection uses the 3DES cipher suite, it will fail if 3DES cipher suites are disabled. Versions TLS 1.0 and 1.1 include cipher suites based on the 3DES algorithm. Office 365 will release TLS 1.0 and 1.1 from June 1, 2020 Worldwide and GCC Locations. Therefore, all combinations of client server and browser server must use TLS 1.2 or 1.2+ to maintain communication with Office 365 resources.
How does this affect me?
Office 365 has established support for TLS 1.0 and 1.1. Microsoft will therefore not fix new issues encountered when connecting Office 365 using TLS 1.0 / 1.1. To ensure uninterrupted access to Office 365 services, you need to update TLS to version 1.2 or later. If you want to get a list of users using TLS 1.0 / 1.1, you can use Microsoft's TLS withdrawal report.

What is the temporary workaround if you are affected?
By this time, you should be affected since Microsoft have start disable small percentage of TLS 1.0 and 1.1 however this is not fully turned off as Microsoft have given less than 2 month grace period to upgrade your application to TLS 1.2 or higher. In 2022, Microsoft plan to disable those older TLS versions to secure the customers and meet compliance requirements. However, due to significant usage, we’ve created an opt-in endpoint that legacy clients can use with TLS1.0 and TLS1.1. This way, an organization is secured with TLS1.2 unless they specifically decide to opt for a less secure posture. Note that only WW customers will be able to use this new endpoint. Customers in US Government clouds have higher security standards and will not be able to opt-in to use older versions of TLS.
To take advantage of this new endpoint, admins will have to:
- Set the AllowLegacyTLSClients parameter on the Set-TransportConfig cmdlet to True.
Set-TransportConfig -AllowLegacyTLSClients $true
- To use Legacy TLS.
Set-TransportConfig -AllowLegacyTLSClients $false
- Legacy clients and devices will need to be configured to submit using the new endpoint
smtp-legacy.office365.com
- Verify by Auditing: Get-TransportConfig | select AllowLegacyTLSClients
Office 365 TLS Deprecation Report:
To make your task easier, Microsoft has provided a new report to track users, devices or applications that use TLS 1.0 / 1.1 or 3DES. You need to be an administrator to extract TLS report. The report provides the following information
- Usernames / IP addresses of users / devices connected to Exchange using TLS 1.0 / 1.1
- Protocol / cipher used for connection - this will be TLS 1.0 / 1.1 or 3DES
- User agent character strings used for this connection - this provides information about the type of device used for the connection
To download a TLS withdrawal report directly, you can use Microsoft's prompt
Alternatively, to download the TLS withdrawal report through Microsoft's secure points portfolio, follow the steps below link: https://servicetrust.microsoft.com/AdminPage/TlsDeprecationReport/Download.
Step1: Login to Microsoft’s secure score and click on “Score Analyzer”.
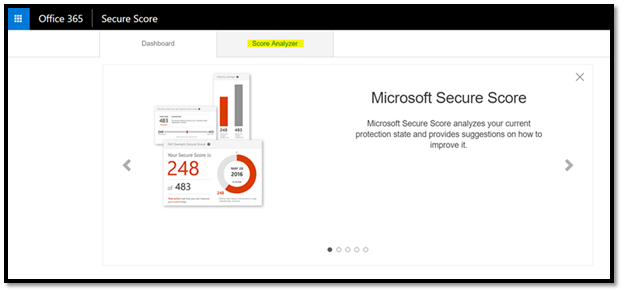
Step 2: Scroll down to 'All Actions'. Search for "Remove TLS 1.0 / 1.1 Dependence and 3DES" for completed actions / Incomplete actions. If you score 5/5, you have already moved to TLS 1.2. else, you need to plan the migration.
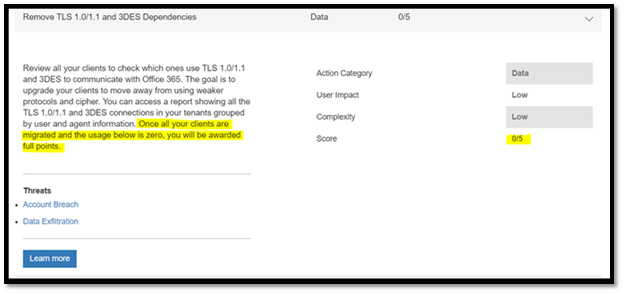
Step 3: Click the ‘Learn More’ button for details on who is connecting using TLS 1.0 / 1.1 or 3DES. It will launch a flyout where you can click on 'Submit Now'.
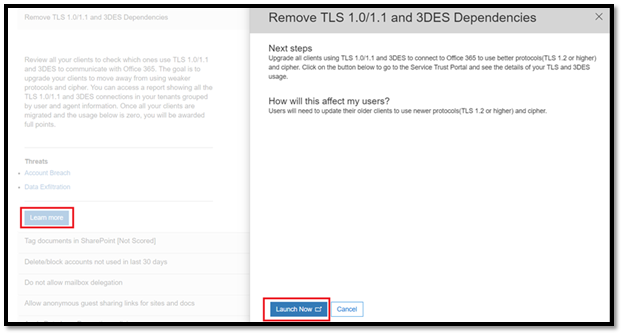
Step 4: 'Present Now' will take you to the Secure Trust Portal (http://servicetrust.microsoft.com). Sign in and click ‘Download’ to get TLS-Deprecation-Report.csv. Or you can use the quick link to download the Office 365 TLS withdrawal report.
Step 5: If you have users or devices listed under TLS1.0 / 1.1, start planning upgrades.
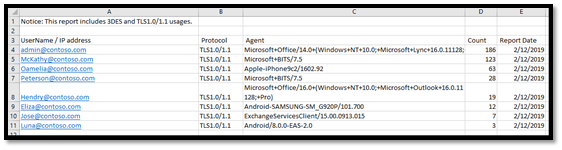
The TLS withdrawal report is updated daily. If you have made any changes and updated any clients / devices, you will need to wait 24 hours to see this change in reports.
As mentioned, you can get a TLS usage report using a TLS withdrawal report. If you need a TLS usage report with more SMTP details on Exchange Online, you can use a TLS usage report from the Security and Compliance Center.
